“Blockchains, Smart Contracts, and the Law” is a comprehensive guide to the legal implications of blockchain technology and smart contracts. The book is suitable for a wide range of audiences, including:
- Lawyers and legal professionals: This book provides a detailed overview of the legal implications of blockchain technology and smart contracts. It covers a wide range of topics, including token assets as money, token assets as property, decentralized finance, token assets as securities, blockchain operations, decentralized autonomous organizations, tokens as real estate, blockchain and open source, and blockchain justice. Legal professionals can use this book to gain a deeper understanding of the legal implications of blockchain technology and smart contracts, and how they can be applied in practice.
- Business executives and entrepreneurs: This book provides a comprehensive overview of the legal implications of blockchain technology and smart contracts, and how they can be used to create new business opportunities. Business executives and entrepreneurs can use this book to gain a deeper understanding of the legal implications of blockchain technology and smart contracts, and how they can be applied to create new business models and revenue streams.
- Blockchain developers and engineers: This book provides a detailed overview of the legal implications of blockchain technology and smart contracts, and how they can be applied in practice. Blockchain developers and engineers can use this book to gain a deeper understanding of the legal implications of blockchain technology and smart contracts, and how they can be applied to create new blockchain-based applications and services.
- Academics and researchers: This book provides a comprehensive overview of the legal implications of blockchain technology and smart contracts, and how they can be applied in practice. Academics and researchers can use this book to gain a deeper understanding of the legal implications of blockchain technology and smart contracts, and how they can be applied to create new research opportunities and areas of study.
- General readers: This book provides a comprehensive overview of the legal implications of blockchain technology and smart contracts, and how they can be applied in practice. General readers interested in blockchain technology and smart contracts and how they are changing the world around us, can use this book to gain a deeper understanding of the legal implications of these technologies

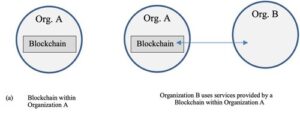
“Blockchains, Smart Contracts, and the Law” is a comprehensive guide to the legal implications of blockchain technology and smart contracts. The book is divided into ten chapters, each of which covers a different aspect of the topic. The first chapter, “Digitization and Remote Agency,” discusses the impact of digital transformations on remote life, signatures, witnesses, and blockchain jurisdiction. The second chapter, “Token Assets as Money,” explores the characteristics of money, US monetary laws, cryptocurrencies as legal tender, monetary malfeasances, agencies of monetary regulation, alternative financial payment and settlement arrangements, and central banks and digital currencies. The third chapter, “Token Assets as Property,” covers token taxation, privacy considerations with blockchain tokens, and references. The fourth chapter, “Decentralized Finance,” compares DeFi vs TradFi/CeFi, decentralized exchanges, and references. The fifth chapter, “Token Assets as Securities,” discusses investments, securities, commodities, token classification tests, token investment performance, and references. The sixth chapter, “Blockchain Operations,” covers blockchain mining/validation and energy, MEV, Flashbots, transaction fees, self-custody & account abstraction, password/account recovery mechanisms, and references. The seventh chapter, “Decentralized Autonomous Organizations,” explains what a DAO is, legal entity status for DAOs, legal issues with DAOs, and references. The eighth chapter, “Tokens as Real Estate,” discusses physical real estate tokens, real estate recordation, virtual real estate tokens, legal issues with real estate transactions via blockchains, and references. The ninth chapter, “Blockchain and Open Source,” covers code repositories, open-source licenses, the role of foundations/non-profits, the role of whitepapers, the role of DAOs, and references. The tenth chapter, “Blockchain Justice,” discusses blockchain dispute resolution and the rise of blockchain ADR mechanisms. Tokens as artworks are discussed in the eleventh chapter, while credential applications are discussed in the twelfth chapter and provenance applications in the thirteenth chapter. The final three chapters cover smart contracts and insurance, estate planning and blockchains, and blockchain voting. The book also includes appendices on hash functions and financial industry terminology.

“Blockchains, Smart Contracts, and the Law” is a comprehensive guide to the legal implications of blockchain technology and smart contracts. This book is an essential resource for anyone who wants to gain a deeper understanding of the legal implications of blockchain technology and smart contracts. Whether you are a lawyer, business executive, entrepreneur, blockchain developer, engineer, academic, researcher, or general readers interested in blockchain technology and smart contracts, this book provides a comprehensive overview of the legal implications of these technologies and how they can be applied in practice. If you are interested in purchasing this book, you can find it on Amazon and other online retailers. The book is available in both paperback and hardback formats. Don’t miss out on this opportunity to gain a deeper understanding of the legal implications of blockchain technology and smart contracts. Order your copy today!

If you are looking for a book that provides a detailed overview of the legal implications of blockchain technology and smart contracts, then “Blockchains, Smart Contracts, and the Law” is the perfect choice for you. This book is written clearly and concisely, making it easy to understand even for those who are new to the topic. The book is divided into sixteen chapters, (and two appendices) each of which covers a different aspect of the topic. Here are some quotes from experts in the field that support the book:
“For a highly readable and reliable roadmap to the blockchain universe you won’t find a better guide than Steven Wright, whose lens captures the scope and details of this world from the heights of the monetary system and tokenomics to the inner workings of bitcoin mining, synthetic derivatives, hash functions and more. I’ll be keeping this encyclopedic work not just in my library for interesting reading, but by my desk as an indispensable guide to this rapidly-evolving landscape.”
Charles N. Bowen
Founder, Legal Path LLC / Adjunct Professor, Georgia State University College of Law